All published articles of this journal are available on ScienceDirect.
Vehicle To Vehicle “V2V” Communication: Scope, Importance, Challenges, Research Directions and Future
Abstract
Day after day Internet of Things (IOT) has become essential in our lives with a lot of research directions and technologies, one of these directions is the Intelligent Transportation System (ITS) which is important for traffic management, and safety. One of its main points is the Vehicle-To-Vehicle (V2V) communication which is essential for the ITS full automated process as it decreases the number of hits between the vehicles and the access points on the roads. V2V is important for the developing countries which does not include Road Side Units (RSUs), so in this research we will go through V2V research directions to explore the current models, and to find out the advantages and challenges of implementing V2V.
1. INTRODUCTION
Transportation is an essential aspect in our life, it is important like food, water, it is impacting our daily lives, but needs to be managed by intelligent systems, one day in the future, it will be managed totally by things not humans, in order to enhance safety, we need to start and improve the V2V and Vehicle-To-Infrastructure “V2I” technologies.
Intelligent Transportation Systems (ITS) is a diverse and expanding subject, with some of its constituents converging or overlapping. For example, transport and travel information might be viewed under a Smart Cities agenda, and similarly “connected cars” are an articulation of Machine-to-Machine (M2M) Communications and the Internet of Things (IOT), V2V communications is usually developed as a part of intelligent transportation systems (ITS) [1].
V2V includes a lot of research directions with no global standardization in the communication model, so at this point there are a lot of points of interest in this topic in order to build a unified commercial communication model.
The main research directions for V2V are the Implementation direction in order to have a real life communication model, Performance evaluation direction in order to have the best KPIs for the V2V communication models, newprotocol design direction in order to have a unified data packet frame, and finally the integration direction in order to have full automated ITS solution.
Vehicle To Vehicle is used to decrease the capacity of the broadcasted information between the Road Side Units and the vehicles, and using it will decrease the high running cost for broadcasting over mobile operator's network [2].
Vehicle To Vehicle network has a number of benefits, but it is important to check and justify what can be achieved from this benefits, for example what is the acceptable number of vehicles per network in order to provide a reliable network performance in addition to its main benefits which are putting the V2V in a preferred position than the Vehicle To Infrastructure network from the cost and load side [2].
Vehicle To Vehicle networks are able to provide a reliable 360 view about what is happening at the road using the full integrated ITS solutions, for example crashes, traffic jams, so it will be better than the currently deployed safety features that are equipped in vehicles like sensors for parking, detection of blind spot.
High mobility of nodes and rapidly changing network topology: In V2V, the connectivity between the vehicles may not be available all the time since the vehicles are moving at different velocities due to which there might be a high mobility and/or quick network changes [3].

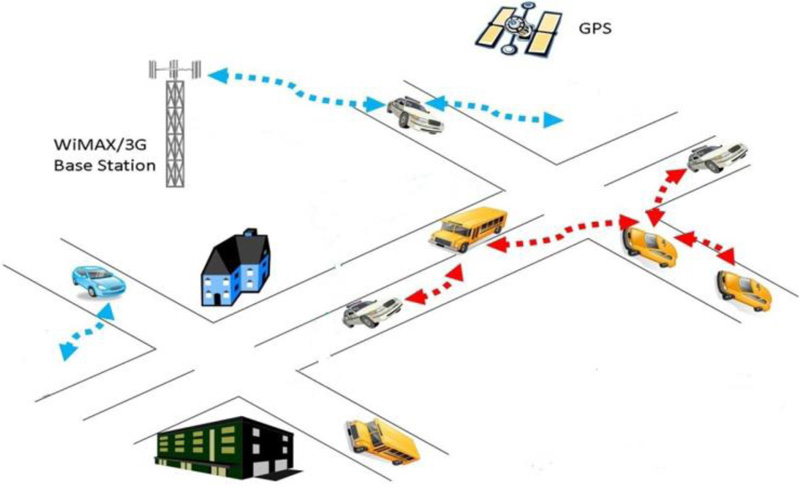
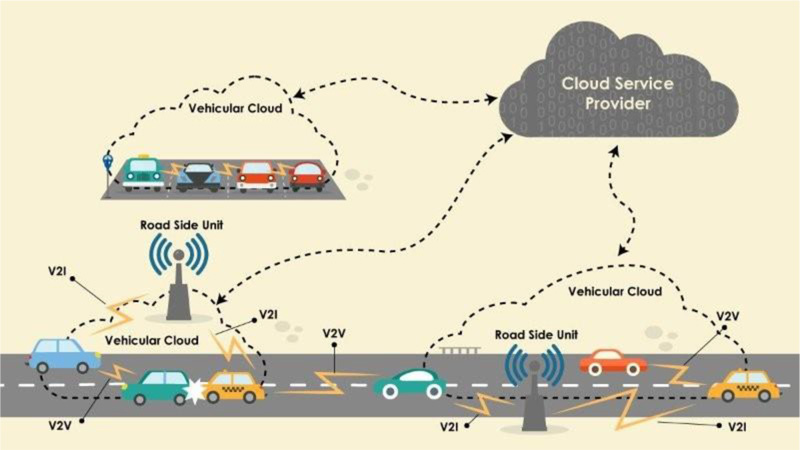
Fig. (1) describes the high level of the V2V communication in a city.
The major challenges to the deployment of V2Vs include defining management and technical structure of the communications-security system, addressing privacy issues, potential unique liability matters and human factors' concerns.
Some researches started on merging many technologies with V2V (V2I, Autonomous Vehicle, etc.) to keep traffic flowing smoothly and safely without the use of any traffic light. Instead of using traditional traffic lights, imagine a number of cars approaching an intersection and communicating among themselves with V2V technology. Together they vote, as it were, and then elect one vehicle to serve as the leader for a certain period, during which it is decided which direction is to be yielded the right of way the, equivalent of a green light and which direction has the red light.
So who has the right of way? It’s very simple and deferential. The leader assigns the status of red light to its own direction of movement while giving the green light to all the cars in the perpendicular flow. After, say, 30 seconds, another car in the perpendicular flow becomes the leader and does the same thing. Thus, leadership is handed over repeatedly, in a round-robin fashion, to fairly share the responsibility and burden because being the leader does involve sacrificing immediate self-interest for the common good.
With this approach, there is no need at all for traffic lights. The work of regulating traffic melts invisibly into the wireless infrastructure. One would never find yourself sitting at a red light when there is no cross traffic to contend with.
In this paper, we will briefly explain IOT and ITS (Section II). In Section III, we will talk about V2V. Then we will discuss the main V2V Research Directions. This research has three important areas; IOT, ITS, V2V and finally V2V over ITS.
2. IOT AND ITS DEFINITIONS
2.1. IOT Definition
The IOT (Internet Of Things) is defined as the intelligent methodology for a dynamic infrastructure related to a global network with features to adjust its configuration automatically based on different types of network protocols where there is an identification for virtual and physical things which are fully integrated using intelligent interfaces with the global data network [5, 6].
Fig. (2) describes where the IOT will be used, and its advantages in our community.
2.2. ITS Definition
Intelligent Transportation Systems (ITS) are evolved programs which, without shaping of AI. For example, the goal to offer modern services mapped to exceptional modes of shipping and management of traffic and allow unique customers to be higher knowledgeable and make extra coordinated, more secure, and to use the network of transportation in a smarter way [7].
Intelligent Transportation System is introduced by the European Union as systems in which conversation and data technologies are used within the track of land transportation, together with automobiles, drivers and infrastructure, and in traffic management and mobility control, in addition to connections with different methods of transportation [8].
The ITS will have a larger scope in the future, probably more in the developing countries than in the developed ones.
3. V2V SCOPE AND VISION
3.1. V2V Scope
Vehicle To Vehicle mechanism is one of the main components in the Vehicular Ad Hoc Network (VANET) networks the main target of which is because of its importance in our daily lives to open direct communication between vehicles. United States is using a predefined band 5.9 GHz. IEEE 802.11p is used as a standard component in United States Vehicle To Vehicle current production implementation.
VANET is considered as Mobile Ad Hoc Network (MANET) with some differences, like considering the vehicle as a node in the network, also the VANET network can include Dedicated Short-Range Communications (DSRC) which are used for V2V mechanism.
Fixed components in the traffic systems are considered as Vehicle To Infrastructure [9].
Fig. (3) describes the high level of the V2V communication in a city.
Table 1 provides the most popular approved V2V applications used by the US Department of Transportation (USDOT).
| V2V Safety | Agency Data/Environment | Smart Roadside/Mobility |
|---|---|---|
| Emergency Electronic Brake Lights (EEBL) | Probe-based Pavement Maintenance | Wireless Inspection |
| Forward Collision Warning (FCW) | Probe-enabled Traffic Monitoring | Smart Truck Parking |
| Intersection Movement Assist (IMA) | Vehicle Classification-based Traffic Studies | Intelligent Traffic Signal System (I-SIG) |
| Left Turn Assist (LTA) | CV-enabled Turning Movement & Intersection Analysis | Signal Priority (transit, freight) |
| Blind Spot/Lane Change Warning | CV-enabled Origin-Destination Studies | Cooperative Adaptive Cruise Control (CACC) |
| Curve Speed Warning | Work Zone Traveler Information | Guidance for Emergency |
| Do Not Pass Warning (DNPW) | Dynamic Eco-Routing (light, vehicle, transit, freight) | Emergency Communications and Evacuation (EVAC) |
| Vehicle Turning Right in Front of | Low Emissions Zone Management | Connection Protection (T-CONNECT) |
| Bus Warning (transit) | Eco-ICM Decision Support System | Freight-Specific Dynamic Travel |
| Queue Warning (Q-WARN) | Eco-Smart Parking | Emergency Vehicle Preemption (PREEMPT) |
3.2. V2V Standard Communication Model
Dedicated Short-Range Communication is the most reliable communication model in Vehicle To Vehicle to supply wireless communications features for ITS programs within a 1 KM range at standard speeds of the highway.
Table 2 provides a comparison of Existing Communication Technologies for V2V Communication from many perspectives (Characteristics, Efficiency, etc.)
3.2.1. DSRC
Dedicated Short-Range Communications is a wireless connection based on mutual way communication. Usually, the range capability is from short to medium which permits the transmission of critical information. The concerned authorities are using a predefined band already reserved for the VANET and approximate variety of 1 KM for use through Intelligent Transportation Systems (ITS) mobility applications and vehicle protection [10].
Vehicle To Infrastructure and Vehicle To Vehicle programs are making use of the Dedicated Short-Range Communication which may additionally have the capacity to seriously reduce the number of the fatal styles of crashes through actual time advisories alerting drivers to pressing risks–like swerving to the road edge closely, cars stopped in advance, impacted lanes all through integration, the existence of nearby cars and communications gadgets [10].
Dedicated Short-Range Communication has become evolved with a major goal of authorizing technology that assists programs for communication and safety between cars and infrastructure to reduce collisions. Dedicated Short-Range Communication is the current exclusive wireless connection with short-range that offers:
- Privacy and Security: Dedicated short-range communication supplies privacy and authentication for safety messages.
- Safety Programs Prioritization: Urgent safety programs are also in a high priority rank more than other programs.
- Flexibility: Dedicated short-range communication ensures that it can combine one or more network methodologies (V2V and V2I) in the same network for safety programs.
- High Accuracy when Required: It is expected that Dedicated Short-range communication works in a very tough work conditions in order to provide high accuracy for the safety programs like high speed vehicles and climate conditions.
- High Acquisition of Network: All connections (new and existent) should be established in an instant mode for safety programs.
- Low Latency: All transmitted data in the VANET should not face any delay by any mean in all vehicular safety programs.
- Particular certified bandwidth: This bandwidth is mandatory to be reserved for safety programs related to vehicles in order to provide secure and reliable communications.
3.2.2. IEEE 802.11p
For a while, Dedicated Short-Range Communication is using IEEE802.11p, The current project which is related to the US DOT depends on the standards related to vehicle-based communication which is based on CALM mechanism (Communication Access for Land Mobiles). It is used especially for programs like Car Safety Services, and ETC gates. The extreme target was a fully integrated national network that authorizes connections between cars and RSUs or other cars [11].
Table 3 describes IEEE802.11 protocol evolution starting from its first version till the current used versions.
IEEE 802.11p is a child version to the main wireless network 802.11 but with some extra features which allow it to support the VANET exclusively to overcome this tough type of networking [11].
The physical and MAC layers are the main layers that include the changes between IEEE 802.11p and 802.11, other layers that are placed at a higher level are not taken into consideration in this change [11].
The IEEE 802.11p uses the Carrier-Sense Multiple Access with Collision Avoidance to support the scenario if a node wants to transmit a data it will check the network medium, and if the medium is available for an AIFS (Arbitration Inter-frame Space), the node should postpone the operation by choosing a random back-off time, all of this is done because EDCA is acting as the MAC method in the IEEE 802.11p which is an advanced DCF version from the main wireless network mechanism [11].
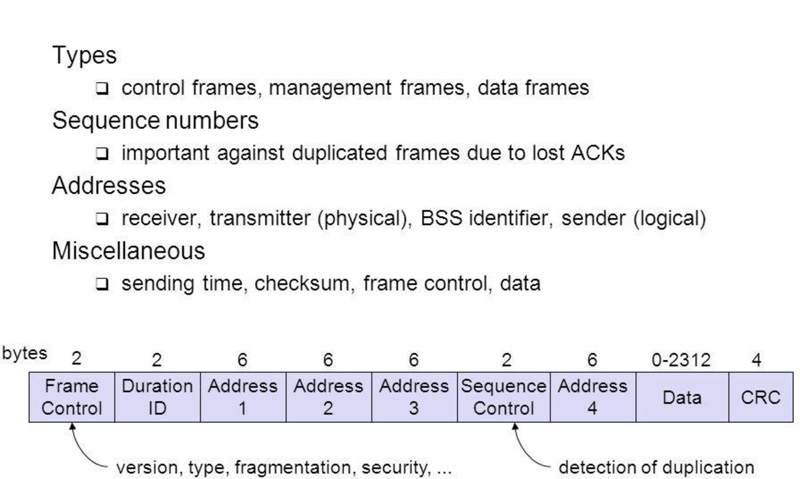
Fig. (4) illustrates the packet frame of IEEE 802.11p and the usage of every bytes range in this packet frame.
| Communication Technologies | Communication Protocols | Range | Characteristics |
|---|---|---|---|
| DSRC | IEEE 802.11p | 1000 m | High Data Transfer Rate Reliable for large networks |
| Infrared | IEEE 802.11 | 10 m | Reliable, mature and easy to master |
| Bluetooth | IEEE 802.15.1 | 10 m | Low Power Good communication Security |
| Wi-Fi | IEEE 802.11a/b/g | 76~305 m | High Data Transfer Rate |
| UWB | IEEE 802.15.3a | 10 m | Strong anti-interference ability |
| Zigbee | IEEE 802.15.4 | 100 m | Low Cost Low Power |
| MmWave | IEEE 802.11ad/IEEE 802.15.3c | 10 m | High Transmission Quality |
| 802.11 Protocol | First Release Date | Max Throughput | Scope |
|---|---|---|---|
| 802.11a | Sep-99 | 54 Mbps | First version based on OFDM |
| 802.11g | Jun-03 | 54 Mbps | Improved performance and range |
| 802.11n | Oct-09 | 150 Mbps | Introduction of MIMO |
| 802.11ac | Dec-13 | 866 Mbps | Increased BW and performance |
| 802.11p | Jul-10 | 54 Mbps | V2X applications |
3.2.3. LTE-V2V
The LTE-V2V technology is a derivative of the cellular uplink technology that maintains similarity with the current LTE systems: frame structure, sub-carrier spacing, clock accuracy requirements and the concept of a resource block, to mention a few. These properties were not made to fit the vehicular use cases, but rather are inherited from existing cellular technology. Consequently, LTE-V2V struggles to meet the specific application requirements of car to car communications.
Commercially, LTE-V2V cannot leverage the presence of the standard LTE modem in the car. Different safety requirements and technology needs strongly suggest that the safety critical domain of LTE-V2V will be separated from the entertainment domain of the standard LTE modem. The stringent synchronization requirements could significantly increase the costs in the LTE-V2V hardware.
Table 4 illustrates the difference between IEEE802.11p and LTE-V2V.
LTE-V2V is a valid alternative and offers a more mature eco-system for entertainment services. The win-win situation would be to focus on the strongest points of each technology and work together to provide the best car-to-car communication solution, continue deploying IEEE802.11p for safety critical applications and ensure that the upcoming LTE-V2V technology can coexist.
4. V2V RESEARCH DIRECTIONS
V2V includes a lot of research directions in many fields, but they share the same concept and point of view to have fully automated traffic management systems and enhance safety.
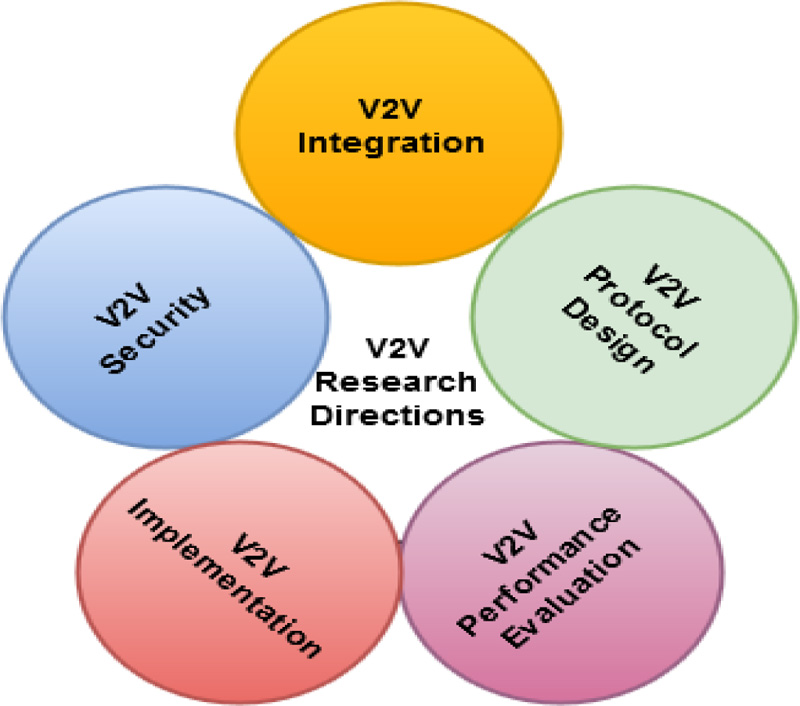
Fig. (5) indicates the main research fields which will be described in detail in the next section.
| - | IEEE802.11p | LTE-V2X |
|---|---|---|
| Multi-user allocation | single user per symbol | multiple users share the same symbol |
| Synchronization requirements | asynchronous | tight synchronization |
| OFDM parameters | short symbol duration | very long symbol duration |
| Channel access mechanism | CSMA-CA | sensing based SPS transmission |
| CP duration | 1.6 µs | 4.69 µs |
| CP purpose | Delay spread | Timing errors, propagation delay, and delay spread |
| Data message | 20 resource blocks (PRBs) | 50 symbols |
| Overhead data | 5 PRBS (2 SA+3 for DTF precoder) | 5 symbols (PLCP+SIGNAL) |
| CP | 4.69 μs | 1.6 μs |
| Pilots | 4 symbols (DMRS) | 4 subcarriers |
| Additional overhead | Guard period (1 symbol) | Service field, tail and padding |
| Total overhead, physical layer | 0.5255 | 0.3397 |
| Transmission duration | Fixed, 1msec | Control (PLCP) = 40 μ sec Data (PSDU) = 50 symbols = 400 μ sec Total = 440 μ sec |
| Occupied bandwidth | Control (SA) = 2 PRB = 360 kHz Data = 2424 PRBs = 4.32 MHz Total = 4.68 MHz |
Fixed, 10 MHz |
| Capacity | ≈ 2 messages / 1ms | ≈ 2 messages / 1ms |
5. V2V RESEARCH DIRECTIONS DESCRIPTION
5.1. V2V Performance Evaluation
In this direction, some researches are talking about performance evaluation based on some protocols like (DSR and AODV) which are designed for Intelligent Transportation System. Some scenarios are related to vehicle to vehicle communication. These scenarios are used to measure the overall execution of the network's output, anatomize the data receiving and sending using the simulation modulators, imitate its connection procedures, so it can show the best practice for enhancing and developing the VANET.
The major performance evaluation KPIs for the V2V are the Packet delay, Packet drop rate, Processing Time, network latency and the amount of radio spectrum [13].
Another paper is talking about the performance evaluation from another perspective, it examines what is the appropriate spectrum range for stable and commercial V2V (vehicle to vehicle) communication in the ITS industry.
The popular characteristic of the traffic safety program is that it makes use of frequent transmissions of messages including the speed and position status of source cars. From their obersvation, two main mechanisms are used for Vehicle To Vehicle, STDMA (Self-Organized Time-Division Multiple Access) and IEEE 802.11p [14].
5.2. V2V Integration
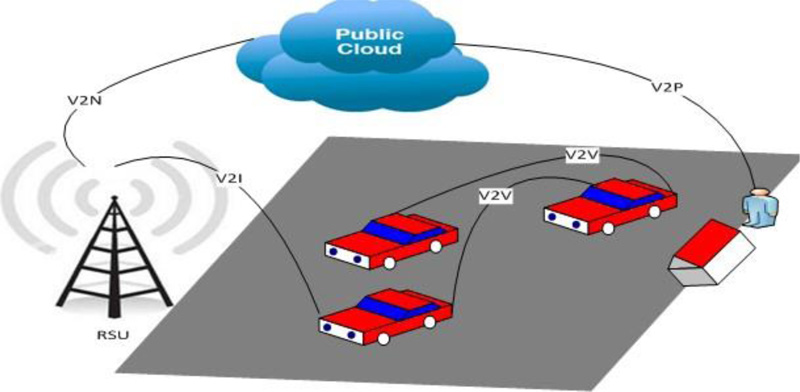
To provide fully automated ITS, V2V may need to integrate with the current computing technologies like cloud computing to get the advantage of a common pool of customizable resources that can interact with low resources of the service provider and doing the provisioning with fewer efforts related to resources management. These resources can be programs, storage and servers [15].
Fig. (6) illustrates the integration of the ITS architecture with the public cloud solutions.
5.3. V2V New Protocol Design
In this direction, some researches are talking about the design of new protocols instead of the currently available protocols, then simulate them on the VANET simulator tools and compare between them and the existent protocols in all directions (Packets Delay, processing Time, Performance, Packets Drop Rate, etc.) to find in the future a suitable standard protocol which is considered as one of the main challenges [17].
The general Steps to design a new V2V protocol are as the following:
- Identify the objective
- Gather the Information
- Study the current V2V protocols (Pros and Cons for each one)
- Study the standard V2V communication model ”If Available”
- Study Protocol Specification
- Design Protocol Interfaces
- Handling Constraints
- Implementation Phase
- Prototype version for testing purposes
- Testing Phase
- Validation Phase
- UAT Phase
Fig. (7) illustrates a high-level work flow for a V2V/V2I protocol.
There is another research talking about the new communication protocol design to enhance road management. It introduces how to manage the critical messages congestion using policies so that the high critical messages will be processed in the highest priority than the less critical messages.
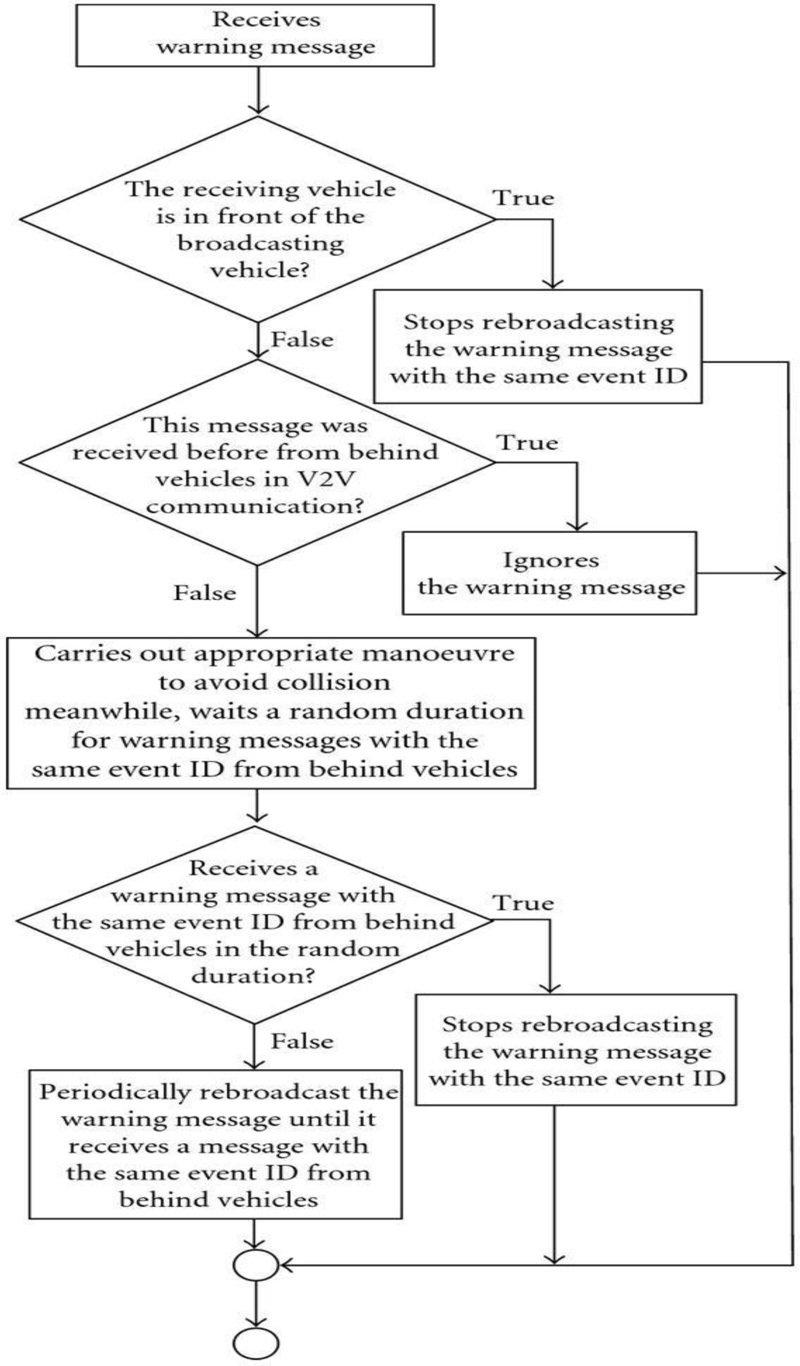
It activates the program of mutual impact warning to use the techniques of service segregation with other programs. It also demonstrates a technique to eliminate excessive critical messages, making use of the flow effect of classic emergency events [19].
5.4. V2V Security
A well-established infrastructure is used for applying continuous security services and securing the critical data related to the Vehicle-To-Vehicle networks.
It demonstrates that security infrastructure techniques are essential for Vehicle-To-Vehicle performance. During the last decade, some researches recommended and tested a method related to performance that able to support the Vehicle-To-Vehicle nodes in a message's acceptance or refusal [20].
Another paper is discussing the impact of the security on the Intelligent Transportation Systems technology, how to ensure that the Vehicle-To-Vehicle networks are safe and secured from all perspectives away from cybersecurity attacks which may lead to fatal crisis’s. Also it is important to let the network users feel comfortable and secured about that their personal data will not be transmitted in any message, also the paper recommended to use the cloud computing systems to save and keep all the data related to the network.
This paper was not recommending the security which is based on an individual mode because the group security mode is more safe and reliable. This means that the cloud computing system is connected to all cells of the network for receiving or sending the data, a number of vehicles will communicate with each other directly and also with the nearest cell that covers the region, and finally the most reliable and strongest connected vehicle in the group with the cell will be the main connector between the cell and the group, this will avoid the dropped messages in case of individual vehicle communication model [21].
The main targets for the security of Vehicle-To-Vehicle researches are based on the following.
- Security Scalability: The V2V network security model should be flexible and able to manage a massive number of vehicles in the network.
- Authenticated Connections: All connections swapped between cars should be authenticated. The authentication system will be responsible of controlling the approved and declined actions passed on a predefined permissions managed by the traffic management center.
- Encrypted Connections: All connections (Send and Receive) between cars must be encrypted. This is covering both synchronous and asynchronous communication models. The credentials of security parameters will be managed and controlled through the transmitted messages to eliminate any hacking trial.
- The V2V must not use any personal data related to the user in any communicated message, just generic safety data and traffic conditions to be sent.
5.5. V2V Implementation Enhancements
This direction is very important as it links between the theoretical and real life, as it implements a V2V on some cities like a prototype in order to develop a road-map for V2V/V2I deployments and business models and realistic deployment strategies to speed-up the market penetration, then to enforce the harmonization of V2V global standards [22].
The output and conclusion for this study have discussed the cooperative collision Avoidance performance vulnerability to unstable communication channels. Also, these results were used to describe and justify the essential requirements for prioritizing the information based on its criticality in the safety programs [23].
6. V2V IMPLEMENTATION “BEST PRACTICE”
In this section, the general V2V hardware design will be discussed including it's main components, going through the description of each component, then talking about the flow of the communication between vehicles, and how the setup model was developed, and finally illustrating the test scenarios (Fig. 8).
The general infrastructure is shown in Fig. (8) includes the below main components:
- Nodes
- Server
- V2V
- V2I
In the general infrastructure, the locations of vehicles are identified through the global positioning system GPS. The event log is transmitted to the traffic management server through the mobile operators GSM/GPRS/3G/4G/5G system that are connected to Internet.
6.1. Main Components Description
6.1.1. Nodes
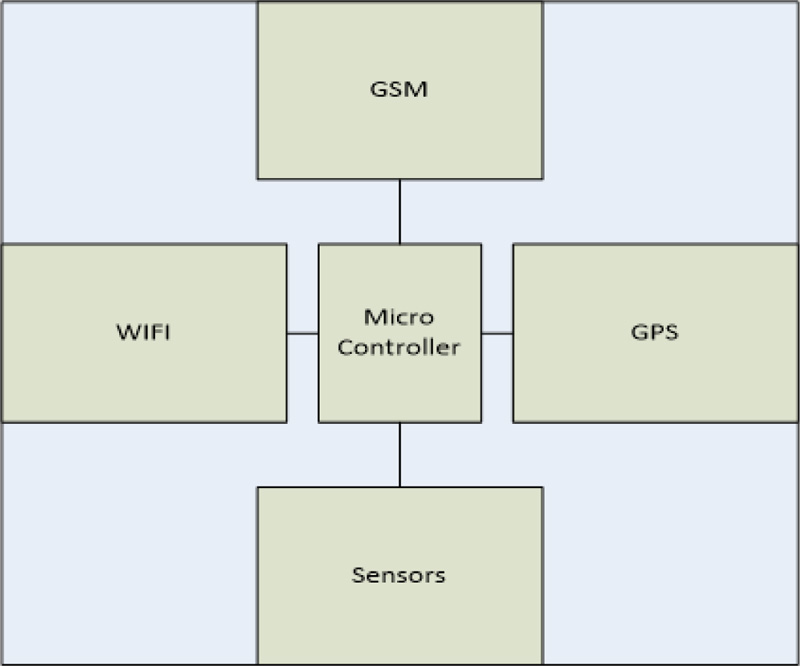
Node means vehicle in our hardware design, each node should support GSM/GPRS/3G/4G/5G Module, GPS Module and WIFI Module. GSM module support data communication through GPRS or 3G/4G. GPRS allows GSM operators to launch wireless data services, such as e-mail and internet access.
GPS module is used on incidents in a variety of ways, such as:
- To determine position locations.
- To navigate from one location to another.
- To create digitized maps.
- To determine distance between two points.
6.1.2. Server
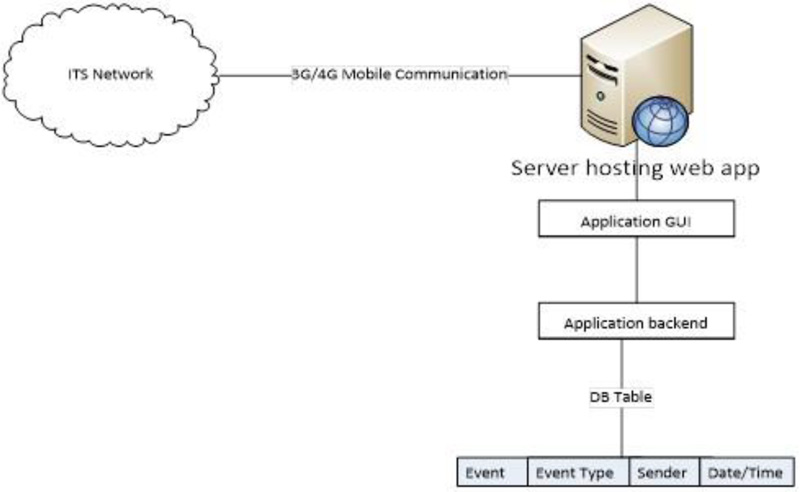
It's a web app and installed it on a local PC (to simulate a server which represent traffic center), to capture the event log in the ITS network through the 3G mobile connection as shown in Fig. (9).
The web application on the server is based on a GUI layer and Backend layer including a small DB to store the event details inside it based on the date, event name, event type, and the sender. The web application is developed in house to provide the exact and required results, also it provides us with a room for expansion to add new features in the future work.
6.1.3. V2V Communication
The communication will be through the WIFI communication between nodes to simulate the real-life events. WIFI and GPS based vehicle location and tracking system will provide effective, real time vehicle location, mapping and reporting this information value and add by improving the level of service provided. A GPS-based vehicle tracking system will inform where your vehicle is and where it has been, how long it has been. The system uses geographic position and time information from the Global Positioning Satellites. The system has an ”On-Board Module” which resides in the vehicle to be tracked. The system uses geographic position and time information from the Global Positioning Satellites. The system has an ”On- Board Module” which resides in the vehicle to be-tracked.
6.1.4. V2I Communication
The communication will be through the GPRS/3G/4G/5G mobile communication between nodes and traffic management server to capture the log events. It provides information gathering and sharing of information on vehicles by the traffic management server. Moreover, it features the processing, computing, sharing and secure release of information onto information platforms. Based on this data, the system can effectively guide and supervise the proposed ITS.
6.2. Node Block Diagram and Architecture
The below diagram is an electronic board which has the main components needed to develop vehicle monitoring unit. Also, this unit can be developed using a mobile application to replace the hardware implementation, because the mobiles are already including most of the hardware unit features like (WIFI, GPS, and GSM modules.) (Fig. 10).
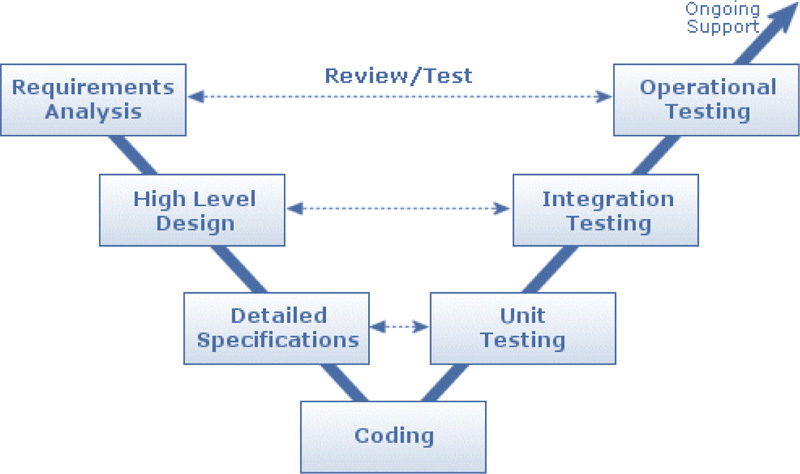
6.3. Software Design
We followed V-Cycle to design the software. An illustration of V-Cycle steps as shown in Fig. (11).
6.3.1. Requirements Analysis
- Complete specification what the software is expected to do.
- The system is expected to send the road status in case of an accident.
6.3.2. High level Design
- Identifying entities within the software and their relationships between each other.
- To achieve the system requirements, we need a micro-controller interfaced with GSM, GPS and Wireless module and a software driver for each unit and software architecture to understand how each unit would act and react with others.
6.3.3. Detailed Specifications
- Where each of the entities scope and behavior are described in details.
- Design the unit driver and the layers based on this driver.
6.3.5. Unit Testing
- In computer programming, unit testing is a method by which individual units (subprogram, object class, pack- age, and module) of source code are tested to determine if they are fit for use.
6.3.6. Integration Testing
- In integration testing the separate modules will be tested together to expose faults in the interfaces and in the interaction between integrated components.
- Testing is usually black box as the code is not directly checked for errors. (Individual software modules are combined and tested as a group).
6.3.7. Operational Testing
- Is the phase of testing used to determine whether a system satisfies the requirements specified in the requirements analysis phase.
- The acceptance test phase is the phase used by the customer to determine whether to accept the software/system or not.
7. V2V FUTURE
In USA, new rules and regulations will be applied to ensure the implementation of the V2V technology as a mandatory requirement which will contribute positively in enhancing the traffic management and the number of accidents. Also, the National Highway Traffic Safety Administration anticipates that providing a full integrated ITS solution will decrease the accidents rate up to 81 percent [25].
Whenever V2V is standard, V2I and the aftermarket will grow opportunistically based on funding, market forces.
In 2015, MIT considered V2V one the main popular and interesting technology sections. In 2017 V2V mechanism was applied in the Cadillac CTS as per General Motors announcement. Also, other manufacturers are trying to increase their investment in this field.
General Motors is dealing with Siemens and Cohda in the infrastructure side to use the same radio band. V2I and V2V applications are supported by VIVE QCA65x4 chipset, X5 LTE modems and Snapdragon X12 which are manufactured by Qualcomm which is one of the popular Chip-makers. Delphi Automotive will implement the V2V technology in many luxury cars like the CTS using the IEEE 802.11p software related to Cohda with NXP’s RoadLINK chipset.
CONCLUSION
Vehicle to Vehicle communication can be a real game changer, because of its importance on our daily lives, it is a major challenge but it will be resolved with time. It includes a lot of points of interest to declare and develop, starting from the protocol design to obtain a standard communication model, then to go through the performance evaluation to have stable KPIs. After that to explore the implementation phase for commercial usage with zero percent failure, and finally to discover the integration mechanisms to release a full automated ITS solution ready to use for the real life.
Vehicle to Vehicle communication real life implementation till now requires RSUs in order to have accurate results and full safety for the society, but due to lack of resources in some of the developing countries most of them don’t have well established infrastructure and on the other side, the accidents and loss of lives are increasing exponentially year by year. Also the developing countries require to increase their investments, and this depends on providing full automated Intelligent Transportation System ”ITS” including V2V communication in order have daily traffic flow without bottlenecks.
LIST OF ABBREVIATIONS
| IOT | = Internet of Things |
| ITS | = Intelligent Transportation System |
| V2I | = Vehicle To Infrastructure |
| V2V | = Vehicle To Vehicle |
| RSU | = Road Side Unit |
| DSR | = Dynamic Source Routing |
| ITU | = International Telecommunication Union |
| IERC | = International Energy Research Centre |
| DSR | = Dynamic Source Routing |
| AODV | = Ad hoc On-Demand Distance Vector |
| VANET | = Vehicular Ad-Hoc Network |
| NHTSA | = National Highway Traffic Safety Administration |
CONSENT FOR PUBLICATION
Not applicable.
FUNDING
None.
CONFLICT OF INTEREST
The authors declare no conflict of interest, financial or otherwise.
ACKNOWLEDGEMENTS
Declared none.


